White Hat on Web Security [Commemorative Edition]
Alibaba group chief technology officer of former President ali cloud jian wang | no founder David feng science and technology | | know UCloud founder JiXin China gen yu founder zhao | small cloud platform, founder of the party's | taobao core technology experts Lin hao joint the testimonials
White hat was not the first time to comb the Web security technology and complete offensive and defensive strategy, as to how to deal with bugs | websites to security, guiding the development of safer Web site, on a large number of industrial safety of actual combat and thinking process | quality analysis.
◎ For the first time, it puts forward the difference between Internet security and traditional security, and provides more targeted solutions. Readers can have the honor to personally hear the first-hand security experience of the direct builders of Ali security technology system from scratch.
Does governs world view | | client script server application | Internet operating several big core security topic, uniqueness to deeply analyze the security nature of ascension in combination with the actual situation the thinking to solve the problem quickly.
Content abstract
In the Internet era, data security and personal privacy are challenged, and various novel attack technologies emerge in an endless stream. How can we better protect our data? White Hat on Web Security (Commemorative Edition) will take you into the world of Web security and introduce you to all aspects of Web security. Hackers are no longer mysterious, attack techniques are so old, small websites can find their own safe path. How do big companies do security, and why do they choose such a solution? You can find the answer in White Hats on Web Security (Commemorative Edition). Detailed analysis, so that you can not only "know", but also "know why".
"White hat on Web security (Commemorative edition)" according to the security treasure Vice president Wu Hanqing in the Internet company before several years of practical work experience and written, in the solution has a strong operability; In-depth analysis of many wrong methods and misunderstandings, security workers have a good reference value; The introduction of security development process and operation also has profound industry guidance significance. The content of the Commemorative Edition is the same as that of the previous edition. It is only for the purpose of commemorating the special edition of the original work which has been published in various languages around the world. Please choose as required.
Author's brief introduction
Wu Hanqing, the founder of the famous domestic security organization Ph4nt0m, is proficient in various attack and defense technologies. He joined Alibaba (China) Co., LTD in 2005 and became a young expert of Alibaba in 2007. Completed the security assessment and security system construction of Alibaba, Taobao and zhi Alipay successively. Led the construction of Alibaba's security development process and has rich experience in the field of application security. He is currently the security architect of Alibaba, responsible for the group's WEB security and cloud computing security.
Inside pages illustrations
Wonderful book review
★ Safety is the statement of the Internet company, but also the basic needs of every netizen, think every day to hear the raw white hat and you share how to care for life, to meet the basic needs, this is a book to taste the taste of gunpowder.
-- Wang Jian, Chief architect of Alibaba Group and president of Alibaba Cloud Computing
★ For the vast majority of small and medium-sized websites, Web security is technically weak and difficult to improve a link, and the problems on this link have made a lot of people sleepless. Thank you for the many valuable lessons shared in this book, which have benefited me greatly. In the meantime, it is highly recommended that every technical team leader read this book. It will benefit you.
-- Feng Dahui, CTO of Lilac Garden
★ As an Internet developer, in the realization of functions also need to focus on how to avoid leaving TXSS, CSRF and other vulnerabilities, otherwise it is easy to appear user account leaks, cross-authority operation and other serious problems, this book explains how to usually website to deal with these vulnerabilities and ensure security, From these valuable practical experience can learn how to better write a secure website.
-- Lin Wu, senior technical expert of Taobao
★ Security has been a nightmare for the Internet, and this book is finally helping us sleep better.
-- Cho Wei, founder and CEO of Choonwoo (icbm)
★ There has always been a lack of technology and thoughtless instruction manual in the security industry. What has been lacking is analysis of the nature of security, thinking about how to better solve the problem in the context of the situation, and sharing of these thoughts. Hanqing Wu is trying to do something, and he has done it.
-- Fang Xiaodun, founder of Wuyun Vulnerability Platform (Jianxin)
directory
Chapter One World View security
Chapter 1 My Security worldview
1 1 Brief history of Web security
1 1 1 A brief history of Chinese hackers
11 2 The development of hacking technology
11 3 The rise of Web security
12 Black hat, white hat
Get back to basics and uncover the nature of security
There is no silver bullet to break superstition
15. Three elements of safety
16 How Do I Perform a Security assessment
16 1 Asset class classification
16 2 Threat analysis
16 3 Risk analysis
16 4 Design a security scheme
The White Hat Art of War
17 1 Secure By Default
17 2 Defense in Depth principle
17 3 Data and code separation principle
17 4 Principle of unpredictability
18 summary
Who will pay for the loopholes?
The second chapter is client-side script security
Chapter 2 Browser Security
21 Same-Origin Policy
22 Sandbox the browser
23 Malicious URL blocking
24 The rapid development of browser security
25 summary
Chapter 3 Cross-site Scripting (XSS)
31 XSS profile
32 Advanced XSS attack
32 1 Explore the XSS Payload
32 2 Powerful XSS Payload
32 3 XSS attack platform
32 4 Ultimate Weapon: XSS Worm
32 5 Debug JavaScript
32 6 XSS Construction Tips
32 7 Turning Waste into Treasure: Mission Impossible
32 8 Overlooked Corners: Flash XSS
32 9 Do you really feel safe: JavaScript Development Frameworks
33 XSS defense
33 1 four two dial a thousand jin: HttpOnly
33 2 Check the input
33 3 Check the output
33 4 Properly defend against XSS
33 5 Process rich text
33 6 Defend the DOM Based on XSS
33 7 Look at the risks of XSS from another perspective
34 summary
Chapter 4 Cross-site Request Forgery (CSRF)
41 CSRF profile
42 CSRF advanced
42 1 Cookie policy of the browser
42 Side effects of 2 P3P head
42 3 GET? POST?
42 4 Flash CSRF
42 5 CSRF Worm
43 CSRF Defense
43 1 Verification code
43 2 Referer Check
43 3 Anti CSRF Token
44 nodules
Chapter 5 ClickJacking
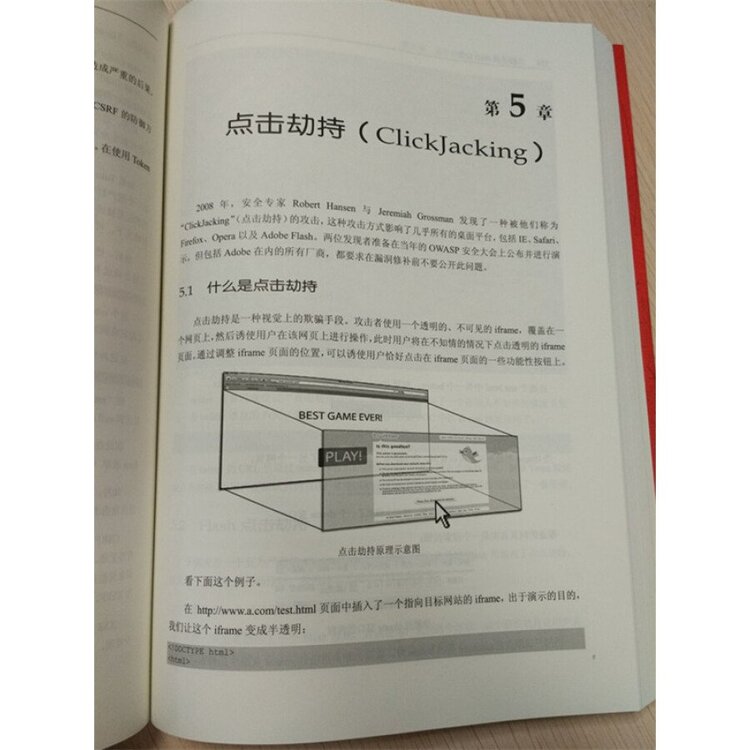
51 What is Clickjacking
52 Flash click hijack
53 Pictures cover the attack
54 Drag hijacking and Data Theft
ClickJacking 30: Touch screen hijacking
56 defense ClickJacking
561 frame busting
562 X-Frame-Options
57 summary
White Hats on Web Security (Commemorative Edition) :
In mid-2010, Mr. Zhang Chunyu from Bowen Viewpoint approached me about writing a book on cloud computing security. At the time, the concept of cloud computing was in the ascendancy, but there was a lack of information on what cloud computing security should do. Due to my work, I have been exposed to this area a lot. However, considering the unclear future of cloud computing and other reasons, I declined Mr. Zhang's request and decided to write a book on Web security instead.
My way to safety
My interest in security originated in middle school. At that time, I bought a hacking manual without ISBN in the pirate market, and coolfire's hacking tutorial impressed me. Since then, in my limited access to the Internet, I have tried my best to find some hacker tutorials and have fun practicing the methods documented in them.
In 2000, I entered Xi 'an Jiaotong University. During my college years, I learned a lot that the school's computer lab was always open to students. At that time, the Internet fee was still relatively expensive, and my parents gave me almost all the living expenses except the necessary living expenses. It was also in the school computer lab that I quickly grew up in this field.
In college, with the financial support of my parents, I got my own personal computer, which accelerated my growth pace. At the same time, with some like-minded friends on the Internet, I started a techno safety organization named after a cartoon I loved at the time: The Phantom Brigade (ph4nt0m.org). After more than ten years, "Phantom" has not been continued due to various reasons, but it has cultivated a lot of good talents in today's security industry in the form of forum. This is my great achievement and pride in my short life of more than 20 years.
Thanks to the openness of the Internet and the good technical communication atmosphere created by me, I have witnessed the development process of almost all Internet security technologies. In the first five years, I devoted a lot of energy to the research of penetration testing technology, buffer overflow technology, network attack technology, etc. In the next five years, due to work needs, I focused on the research of Web security.
Join Alibaba
This change of professional direction happened because I joined Alibaba in 2005 on the recommendation of a close friend.
The process of joining the company was legendary. During the interview, I was asked by my supervisor to demonstrate my ability, so I remotely shut down a routing device of an upstream operator on Alibaba's internal network, causing an interruption of Alibaba's internal network. The supervisor immediately asked the operator to re-sign the availability agreement.
My parents were shocked that my college hobby could turn into a serious career (many universities didn't offer courses or majors in cybersecurity at that time), and it only strengthened my own idea of making a career out of it.
In Alibaba, I quickly rose to prominence. I once caught the email password of the development director through network sniffing in the Intranet. It took down the company's network in a flash during a stress test; On several occasions, I managed to gain access to the domain control server, allowing me to access any employee's computer as an administrator.
But these work results, are far less than the thick pile of website security assessment report let me more sense of achievement, because I know that every vulnerability on the website, are affecting thousands of users. It makes me proud to serve millions and millions of Internet users. At that time, the Web was gradually becoming the core of the Internet, and the Web security technology was also rising, so I committed myself to the research of Web security.
I became a very young technical expert in Alibaba Group in 2007 at the age of 23. There are no official statistics, but I was probably one of the best young technologists in the group, and I was awarded this award in 2010. At Alibaba, I have been privileged to witness the building of the security department from scratch. At the same time, Taobao and Alipay have not yet established their own security team, so I have the honor to participate in the security construction of Taobao and Alipay, laying the foundation for their security development framework and security development process.
Thoughts on Internet security
At that time, I vaguely felt the Internet company security, and the traditional network security, information security technology difference. Just like the challenges developers face, there are many problems that are difficult to expose without being exposed to a large number of users. Because quantitative change causes qualitative change, managing 10 servers is going to be different than managing 10,000 servers. Similarly, evaluating the code security of 10 engineers must be done differently than evaluating the code security of 1,000 engineers.
Internet company security also has some distinct features, such as user experience, performance and product release time, so traditional security solutions may be close to impossible in such an environment. This has put forward higher requirements and greater challenges to the safety work.
These problems make me feel that Internet company security may become a new discipline, or security technology should become more industrial. But when I was in bookstores, I found security books that were either very academic (unreadable) textbooks or very entertaining (such as some "hacker tool manual" type books) manuals. There are very few books that delve into the principles of safety technology, and in my experience, there are all sorts of problems in an industrial environment.
These questions prompted me to write a book of my own to share my work experience over the years. It will be a book that explains the practice of security technology in enterprise applications, a security reference book that engineers at large Internet companies can really use. So when Mr. Zhang mentioned the idea of inviting me to write a book, I said yes without much thought.
Web is the core of the Internet and a good carrier of cloud computing and mobile Internet in the future, so Web security is also a very important part of the security business of Internet companies. My research focus in recent years also lies in this, so I choose Web security as my topic. But in fact, many of the book's ideas are not limited to Web security, but can be relaxed to the entire Internet security aspects.
If you have the right way of thinking about security issues, you will be able to solve them without any obstacles. When I was in 2007, aware of the importance of the master the correct way of thinking, so I told friends: safety engineer's core competence is not how much he can have a zero day, master many kinds of security technology, but rather in his deep understanding of security, and the extension of the view Angle and the height of the safety problem. That's what I think and that's what I do.
So what I think is valuable in this book is not the industrial solutions, but the thought processes that go into solving these problems. We are not trying to make a solution that will solve the problem, but to make a solution that will "beautifully" solve the problem. This is the pursuit of every good safety engineer.
Security Enlightenment
However, in today's Internet industry, the emphasis on security is generally not high. Statistics show that Internet companies spend less than one percent of their revenue on security.
At the end of 2011, the Chinese Internet suddenly became embroiled in one of the biggest security crises in history. On December 21st CSDN, a large developer community, was hacked and the data of 6m registered users was released on the Internet. more