Internet Security Book Recommendations
What is penetration testing? What is the strategic approach to learning penetration testing? What are the specific ways to learn penetration testing? How to solve various problems encountered? 1. Do you need to learn programming for penetration? 2. What is the thinking of penetration testing? 3. Who do you ask if you have any questions? How to ask? 4. The problem of penetration tools. 5. Questions about infiltration of actual combat. 6. How much do you need to learn to go to work... Come to us to give you the answer!
8个产品
-
White Hat on Web Security [Commemorative Edition]
(1篇评论)10.00 USDAlibaba group chief technology officer of former President ali cloud jian wang | no founder David feng science and technology | | know UCloud founder JiXin China gen yu founder zhao | small cloud platform, founder of the party's | taobao core technology experts Lin hao joint the testimonials
White hat was not the first time to comb the Web security technology and complete offensive and defensive strategy, as to how to deal with bugs | websites to security, guiding the development of safer Web site, on a large number of industrial safety of actual combat and thinking process | quality analysis.
◎ For the first time, it puts forward the difference between Internet security and traditional security, and provides more targeted solutions. Readers can have the honor to personally hear the first-hand security experience of the direct builders of Ali security technology system from scratch.
Does governs world view | | client script server application | Internet operating several big core security topic, uniqueness to deeply analyze the security nature of ascension in combination with the actual situation the thinking to solve the problem quickly.
Content abstract
In the Internet era, data security and personal privacy are challenged, and various novel attack technologies emerge in an endless stream. How can we better protect our data? White Hat on Web Security (Commemorative Edition) will take you into the world of Web security and introduce you to all aspects of Web security. Hackers are no longer mysterious, attack techniques are so old, small websites can find their own safe path. How do big companies do security, and why do they choose such a solution? You can find the answer in White Hats on Web Security (Commemorative Edition). Detailed analysis, so that you can not only "know", but also "know why".
"White hat on Web security (Commemorative edition)" according to the security treasure Vice president Wu Hanqing in the Internet company before several years of practical work experience and written, in the solution has a strong operability; In-depth analysis of many wrong methods and misunderstandings, security workers have a good reference value; The introduction of security development process and operation also has profound industry guidance significance. The content of the Commemorative Edition is the same as that of the previous edition. It is only for the purpose of commemorating the special edition of the original work which has been published in various languages around the world. Please choose as required.
Author's brief introductionWu Hanqing, the founder of the famous domestic security organization Ph4nt0m, is proficient in various attack and defense technologies. He joined Alibaba (China) Co., LTD in 2005 and became a young expert of Alibaba in 2007. Completed the security assessment and security system construction of Alibaba, Taobao and zhi Alipay successively. Led the construction of Alibaba's security development process and has rich experience in the field of application security. He is currently the security architect of Alibaba, responsible for the group's WEB security and cloud computing security.
Inside pages illustrations
Wonderful book review
★ Safety is the statement of the Internet company, but also the basic needs of every netizen, think every day to hear the raw white hat and you share how to care for life, to meet the basic needs, this is a book to taste the taste of gunpowder.
-- Wang Jian, Chief architect of Alibaba Group and president of Alibaba Cloud Computing
★ For the vast majority of small and medium-sized websites, Web security is technically weak and difficult to improve a link, and the problems on this link have made a lot of people sleepless. Thank you for the many valuable lessons shared in this book, which have benefited me greatly. In the meantime, it is highly recommended that every technical team leader read this book. It will benefit you.
-- Feng Dahui, CTO of Lilac Garden★ As an Internet developer, in the realization of functions also need to focus on how to avoid leaving TXSS, CSRF and other vulnerabilities, otherwise it is easy to appear user account leaks, cross-authority operation and other serious problems, this book explains how to usually website to deal with these vulnerabilities and ensure security, From these valuable practical experience can learn how to better write a secure website.
-- Lin Wu, senior technical expert of Taobao★ Security has been a nightmare for the Internet, and this book is finally helping us sleep better.
-- Cho Wei, founder and CEO of Choonwoo (icbm)★ There has always been a lack of technology and thoughtless instruction manual in the security industry. What has been lacking is analysis of the nature of security, thinking about how to better solve the problem in the context of the situation, and sharing of these thoughts. Hanqing Wu is trying to do something, and he has done it.
-- Fang Xiaodun, founder of Wuyun Vulnerability Platform (Jianxin)
directoryChapter One World View security
Chapter 1 My Security worldview
1 1 Brief history of Web security
1 1 1 A brief history of Chinese hackers
11 2 The development of hacking technology
11 3 The rise of Web security
12 Black hat, white hat
Get back to basics and uncover the nature of security
There is no silver bullet to break superstition
15. Three elements of safety
16 How Do I Perform a Security assessment
16 1 Asset class classification
16 2 Threat analysis
16 3 Risk analysis
16 4 Design a security scheme
The White Hat Art of War
17 1 Secure By Default
17 2 Defense in Depth principle
17 3 Data and code separation principle
17 4 Principle of unpredictability
18 summary
Who will pay for the loopholes?The second chapter is client-side script security
Chapter 2 Browser Security
21 Same-Origin Policy
22 Sandbox the browser
23 Malicious URL blocking
24 The rapid development of browser security
25 summaryChapter 3 Cross-site Scripting (XSS)
31 XSS profile
32 Advanced XSS attack
32 1 Explore the XSS Payload
32 2 Powerful XSS Payload
32 3 XSS attack platform
32 4 Ultimate Weapon: XSS Worm
32 5 Debug JavaScript
32 6 XSS Construction Tips
32 7 Turning Waste into Treasure: Mission Impossible
32 8 Overlooked Corners: Flash XSS
32 9 Do you really feel safe: JavaScript Development Frameworks
33 XSS defense
33 1 four two dial a thousand jin: HttpOnly
33 2 Check the input
33 3 Check the output
33 4 Properly defend against XSS
33 5 Process rich text
33 6 Defend the DOM Based on XSS
33 7 Look at the risks of XSS from another perspective
34 summaryChapter 4 Cross-site Request Forgery (CSRF)
41 CSRF profile
42 CSRF advanced
42 1 Cookie policy of the browser
42 Side effects of 2 P3P head
42 3 GET? POST?
42 4 Flash CSRF
42 5 CSRF Worm
43 CSRF Defense
43 1 Verification code
43 2 Referer Check
43 3 Anti CSRF Token
44 nodulesChapter 5 ClickJacking
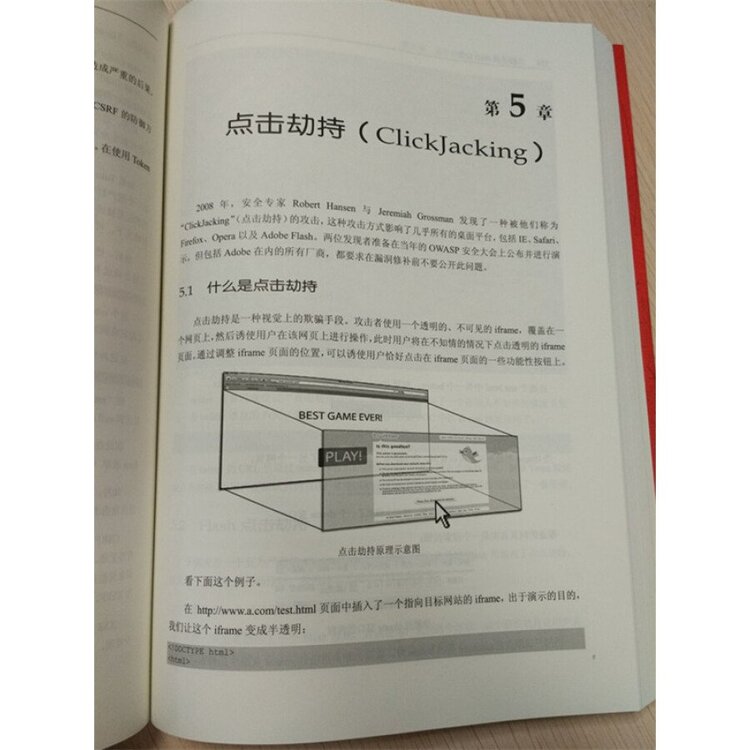
51 What is Clickjacking
52 Flash click hijack
53 Pictures cover the attack
54 Drag hijacking and Data Theft
ClickJacking 30: Touch screen hijacking
56 defense ClickJacking
561 frame busting
562 X-Frame-Options
57 summaryWhite Hats on Web Security (Commemorative Edition) :
In mid-2010, Mr. Zhang Chunyu from Bowen Viewpoint approached me about writing a book on cloud computing security. At the time, the concept of cloud computing was in the ascendancy, but there was a lack of information on what cloud computing security should do. Due to my work, I have been exposed to this area a lot. However, considering the unclear future of cloud computing and other reasons, I declined Mr. Zhang's request and decided to write a book on Web security instead.
My way to safety
My interest in security originated in middle school. At that time, I bought a hacking manual without ISBN in the pirate market, and coolfire's hacking tutorial impressed me. Since then, in my limited access to the Internet, I have tried my best to find some hacker tutorials and have fun practicing the methods documented in them.
In 2000, I entered Xi 'an Jiaotong University. During my college years, I learned a lot that the school's computer lab was always open to students. At that time, the Internet fee was still relatively expensive, and my parents gave me almost all the living expenses except the necessary living expenses. It was also in the school computer lab that I quickly grew up in this field.
In college, with the financial support of my parents, I got my own personal computer, which accelerated my growth pace. At the same time, with some like-minded friends on the Internet, I started a techno safety organization named after a cartoon I loved at the time: The Phantom Brigade (ph4nt0m.org). After more than ten years, "Phantom" has not been continued due to various reasons, but it has cultivated a lot of good talents in today's security industry in the form of forum. This is my great achievement and pride in my short life of more than 20 years.
Thanks to the openness of the Internet and the good technical communication atmosphere created by me, I have witnessed the development process of almost all Internet security technologies. In the first five years, I devoted a lot of energy to the research of penetration testing technology, buffer overflow technology, network attack technology, etc. In the next five years, due to work needs, I focused on the research of Web security.
Join Alibaba
This change of professional direction happened because I joined Alibaba in 2005 on the recommendation of a close friend.
The process of joining the company was legendary. During the interview, I was asked by my supervisor to demonstrate my ability, so I remotely shut down a routing device of an upstream operator on Alibaba's internal network, causing an interruption of Alibaba's internal network. The supervisor immediately asked the operator to re-sign the availability agreement.
My parents were shocked that my college hobby could turn into a serious career (many universities didn't offer courses or majors in cybersecurity at that time), and it only strengthened my own idea of making a career out of it.
In Alibaba, I quickly rose to prominence. I once caught the email password of the development director through network sniffing in the Intranet. It took down the company's network in a flash during a stress test; On several occasions, I managed to gain access to the domain control server, allowing me to access any employee's computer as an administrator.
But these work results, are far less than the thick pile of website security assessment report let me more sense of achievement, because I know that every vulnerability on the website, are affecting thousands of users. It makes me proud to serve millions and millions of Internet users. At that time, the Web was gradually becoming the core of the Internet, and the Web security technology was also rising, so I committed myself to the research of Web security.
I became a very young technical expert in Alibaba Group in 2007 at the age of 23. There are no official statistics, but I was probably one of the best young technologists in the group, and I was awarded this award in 2010. At Alibaba, I have been privileged to witness the building of the security department from scratch. At the same time, Taobao and Alipay have not yet established their own security team, so I have the honor to participate in the security construction of Taobao and Alipay, laying the foundation for their security development framework and security development process.
Thoughts on Internet security
At that time, I vaguely felt the Internet company security, and the traditional network security, information security technology difference. Just like the challenges developers face, there are many problems that are difficult to expose without being exposed to a large number of users. Because quantitative change causes qualitative change, managing 10 servers is going to be different than managing 10,000 servers. Similarly, evaluating the code security of 10 engineers must be done differently than evaluating the code security of 1,000 engineers.
Internet company security also has some distinct features, such as user experience, performance and product release time, so traditional security solutions may be close to impossible in such an environment. This has put forward higher requirements and greater challenges to the safety work.
These problems make me feel that Internet company security may become a new discipline, or security technology should become more industrial. But when I was in bookstores, I found security books that were either very academic (unreadable) textbooks or very entertaining (such as some "hacker tool manual" type books) manuals. There are very few books that delve into the principles of safety technology, and in my experience, there are all sorts of problems in an industrial environment.
These questions prompted me to write a book of my own to share my work experience over the years. It will be a book that explains the practice of security technology in enterprise applications, a security reference book that engineers at large Internet companies can really use. So when Mr. Zhang mentioned the idea of inviting me to write a book, I said yes without much thought.
Web is the core of the Internet and a good carrier of cloud computing and mobile Internet in the future, so Web security is also a very important part of the security business of Internet companies. My research focus in recent years also lies in this, so I choose Web security as my topic. But in fact, many of the book's ideas are not limited to Web security, but can be relaxed to the entire Internet security aspects.
If you have the right way of thinking about security issues, you will be able to solve them without any obstacles. When I was in 2007, aware of the importance of the master the correct way of thinking, so I told friends: safety engineer's core competence is not how much he can have a zero day, master many kinds of security technology, but rather in his deep understanding of security, and the extension of the view Angle and the height of the safety problem. That's what I think and that's what I do.
So what I think is valuable in this book is not the industrial solutions, but the thought processes that go into solving these problems. We are not trying to make a solution that will solve the problem, but to make a solution that will "beautifully" solve the problem. This is the pursuit of every good safety engineer.
Security Enlightenment
However, in today's Internet industry, the emphasis on security is generally not high. Statistics show that Internet companies spend less than one percent of their revenue on security.
At the end of 2011, the Chinese Internet suddenly became embroiled in one of the biggest security crises in history. On December 21st CSDN, a large developer community, was hacked and the data of 6m registered users was released on the Internet. more -
Hacker Secrets Practical guide to penetration testing
(1篇评论)8.00 USDExcellent reputation on the market penetration test books, in the field of test books in the United States ranked the first, the reader's good reviews, sales second kill all other similar penetration test books.
The tactics of penetration testing, described in rugby lingo, are as follows.
Preparation - Installation: This chapter describes how to set up the lab, attack host, and tools used throughout the book.
Before serving - Scan the network: Before carrying out various operations, you need to carefully check the environment and understand the situation. We will take you to discover and intelligently scan the target system.
Dribbling - Exploit: Infiltrate the target system based on the vulnerabilities found in Chapter 2. In this chapter, we need manual practices to penetrate the target system.
Toss - Manual detection techniques for Web applications: Sometimes you need to get creative when finding targets that are publicly available on the Internet. We'll delve into how to manually search and attack web applications.
Cross transmission - Penetration of the Intranet: After a system has been breached, various methods for horizontal penetration of the network will be discussed.
Assists -- Social Engineering: Deceiving opponents through play. This chapter will explain some social engineering strategies.
Short Pass - Physical Access Attack: A good short pass requires a short distance. In this section, physical attack methods are introduced.
Quarterback Break - Evade antivirus detection: The quarterback break is ideal when only a few yards away. Sometimes you cannot escape the anti-virus software. This chapter describes how to avoid the anti-virus software and overcome the above obstacles.
Secret Service Groups - Cracking, Exploiting and Techniques: Cracking codes, exploiting vulnerabilities, Nethunters and some techniques.
Two-minute drill - Go from Zero to Hero: You only have two minutes to go from no access rights to very high domain administrator rights.
Post-match -- Analysis report: Write the penetration test report and report the results.
Continuing education: Share with your readers some of the things you need to do to improve penetration testing.Content abstract
Hacker Tips -- The Practical Guide to Penetration Testing (2nd Edition) is a new and updated version of the bestselling Hacker Tips -- The Practical Guide to Penetration Testing. It completely updates the previous edition and adds a lot of new knowledge. The book uses real-world examples and helpful advice to explain some of the obstacles you face during penetration testing and how to overcome them.
The hacking tips - penetration test practical guide (2nd edition), which is divided into 12 chapters, covering against the installation of the machine/tool configuration, network scanning, and the exploit, artificial detection technology of web applications, network, social engineering skills, physical access to attack, to evade antivirus software testing method, Tips on cracking passwords and analysis reports, continuing education and other knowledge.
The Hacker Secret -- A Practical Guide to Penetration Testing (2nd Edition) is organized and independent of each other so that readers can read it either on demand or chapter by chapter. A background in penetration testing is not required, but relevant experience is helpful in understanding the content of this book.Author's brief introduction
Peter Kim is the CEO and Chairman of Secure Planet. He has nearly 10 years of experience in the security field and has been engaged in penetration testing for the past 7 years. He has taught courses in penetration testing and cybersecurity at Howard Community College in Maryland and holds numerous security-related certifications.
directory
Chapter 1 Preparation -- Installation 1
1.1 Setting up a Test Environment 1
1.2 Creating a domain 1
1.3 Creating Other Servers 2
1.4 Practice 2
1.5 Build penetration test environment 3
1.5.1 Installing a Penetration Test Environment 3
1.5.2 Hardware 4
1.5.3 Open Source and Commercial Software 5
1.5.4 Establishing the Platform 6
1.5.5 Setting up Kali Linux 8
1.5.6 Windows VM 17
1.5.7 Setting the Windows Environment 18
1.5.8 Starting PowerShell 20
1.5.9 Easy-P 22
1.6 Learning 24
1.6.1 Metasploitable 2 24
1.6.2 Binary utilization 26
1.7 Summary 36Chapter 2 Before serving -- Scan the network 37
2.1 Passive Information Search - Open Source Intelligence (OSINT) 37
2.1.1 Recon-NG (https://bitbucket.org/LaNMaSteR53/recon-ng,
Kali Linux) 38
2.1.2 Discover script (https://github.com/leebaird/discover, Kali Linux) 42
2.1.3 SpiderFoot (http://www.spiderfoot.net/, Kali Linux) 44
2.2 Creating a Password Dictionary 46
2.2.1 Wordhound (https://bitbucket.org/mattinfosec/wordhound.git,
Kali Linux) 46
2.2.2 BruteScrape (https://github.com/cheetz/brutescrape, Kali Linux) 50
2.2.3 Use the hack password list to find email addresses and credentials 51
2.2.4 Gitrob -- Github Analysis (https://github.com/michenriksen/gitrob,
Kali Linux) 54
2.2.5 Open-source intelligence data collection 56
2.3 External or internal active information collection 57
2.3.1 Masscan (https://github.com/robertdavidgraham/masscan, Kali Linux) 57
2.3.2 SPARTA (http://sparta.secforce.com/, Kali Linux) 60
2.3.3 HTTP Screenshot (https://github.com/breenmachine/httpscreenshot,
Kali Linux) 63
2.4 Vulnerability Scan 67
2.4.1 Rapid7 Nexpose/Tenable Nessus (Kali/Windows/OS X) 67
2.4.2 OpenVAS(http://www.openvas.org/, Kali) 68
2.5 Website Application Scan 71
2.5.1 Scanning websites 71
2.5.2 Website application Scan 72
2.5.3 OWASP Zap Proxy(https://code.google.com/p/zaproxy/,
Kali Linux/Windows/OS X) 79
2.6 Analyze Nessus, Nmap, and Burp 81
2.7 Summary 83Chapter 3 Dribbling the Ball -- Exploit the Hole 85
3.1 Metasploit(http://www.metasploit.com, Windows/Kali Linux) 85
3.1.1 Starting the Metasploit Tool from a Terminal of the Kali Operating System 86 Initialize and start the Metasploit tool
3.1.2 Run Metasploit 86 Using the Common Configuration Command
3.1.3 Running Metasploit - Exploit subsequent operations or other 87
3.1.4 Using the Metasploit platform to exploit Vulnerability MS08-067 87
3.2 Script 89
3.3 Printer 90
3.4 Heartbleed 94
3.5 Shellshock 97
3.6 Exporting Git Code Base (Kali Linux) 101
3.7 Nosqlmap (www.nosqlmap.net/, Kali Linux) 103
3.8 Elastic Search (Kali Linux) 106
3.9 Summary 108Chapter 4 Toss -- Manual detection techniques for Web Applications 109
4.1 Web Application Penetration Test 110
4.1.1 SQL Injection 111
4.1.2 Manual SQL injection 115
4.1.3 Cross-site Scripting (XSS) 131
4.1.4 Cross-site Request Forgery (CSRF) 136
4.1.5 Session token 139
4.1.6 Other Fuzzy Test/Input Verification 141
4.1.7 Other Top 10 OWASP Vulnerabilities 144
4.1.8 Functional/Business Logic Test 146
4.2 Summary 147Chapter 5 Cross Transmission -- Penetrating the Intranet 149
5.1 Network Penetration without Credentials 149
5.1.1 Responder. py (https://github.com/SpiderLabs/Responder, Kali Linux) 149
5.1.2 ARP Deception 153
5.1.3 Cain and Abel (http://www.oxid.it/cain.html, Windows) 154
5.1.4 Ettercap(http://ettercap.github.io/ettercap/, Kali Linux) 156
5.1.5 Backdoor Factory Agent (https://github.com/secretsquirrel/ BDFProxy,
Kali Linux) 157
5.1.6 Attack Operations after ARP spoofing 159
5.2 Using Arbitrary domain Credentials (non-administrator rights) 167
5.2.1 Conducting System Reconnaissance 167
5.2.2 Group Policy Preference 173
5.2.3 A note on the late exploitation of the vulnerability 175
5.2.4 Promoting Permission 176
5.3 Having Local Administrator Rights or Domain Administrator Rights 181
5.3.1 Infiltrate the entire Network Using Credentials and psexec 182
5.3.2 Executing Commands on Multiple Hosts Using the psexec Tool (Kali Linux) 185
5.3.3 Using the WMI Tool for Horizontal Penetration (Windows) 186
5.3.4 Kerberos-MS14-068 188
5.3.5 Pass ticket Attack 190
5.3.6 Horizontal Infiltration Using the PostgreSQL Vulnerability 192
5.3.7 Obtaining the Cache Certificate 195
5.4 Attacking Domain Controller 197
5.4.1 SMBExec(https://github.com/brav0hax/smbexec, Kali Linux) 197
5.4.2 psexec_ntdsgrab (Kali Linux) 199
5.5 Continuous Control 201
5.5.1 Veil and PowerShell 201
5.5.2 Implementing Continuous Control Using Scheduled Tasks 204
5.5.3 Gold Note 206
5.5.4 Universal Key 213
5.5.5 Viscous bond 215
5.6 Summary 218Chapter 6 Assists -- Social Engineering 219
6.1 Approximate domain name 219
6.1.1 SMTP Attack 219
6.1.2 SSH Attack 220
6.2 Phishing 222
6.3 Phishing Report 231Chapter 7 Short Passing -- Physical Access Attacks 233
7.1 Wireless Network Penetration 233
7.1.1 Passive Identification and Reconnaissance 233
7.1.2 Active Attack 235
7.2 Worker Card Clone 245
7.3 Kon-boot(http://www.piotrbania.) com/all/kon-boot /, Windows/OS X) 249
7.3.1 Windows 250
7.3.2 OS X 250
7.4 Penetration Test Portable Device - Raspberry Pi 2 251
7.5 Rubber Ducky (http://hakshop.myshopify.com/ products/ usb-rubber-ducky -
deluxe) 255
7.6 Summary 258Chapter 8 Quarterback Breakout -- Circumventing anti-virus detection 259
8.1 Avoiding Antivirus Software 259
8.1.1 Back Door Factory (https://github.com/secretsquirrel/the-backdoorfactory,
Kali Linux) 259
8.1.2 WCE Evading Detection by Anti-virus Software (Windows) 263
8.1.3 Veil (https://github.com/Veil-Framework, Kali Linux) 267
8.1.4 SMBExec (https://github.com/pentestgeek/smbexec, Kali Linux) 270
8.1.5 peCloak. py(http://www.securitysift.com/pecloak-py-an-experiment-in -
Av - evasion/Windows) 272
8.1.6 Python 274
8.2 Other Keyboard Logging Tools 276
8.2.1 Use Nishang Keylogging tool (https://github.com/ samratashok/)
nishang) 277
8.2.2 Using Keylogging in PowerSploit (https://github.com/ mattifestation/)
PowerSploit) 278
8.3 Summary 278Chapter 9 The Secret Service -- Hacking, Exploitation, and Techniques 2
-
Red and blue attack and defense: Building a real combat network security defense system
(1篇评论)9.00 USDThis is a book from the perspective of the red team, the blue team, the purple team to comprehensively explain how to carry out the red and blue attack and defense practice, is a summary of the experience of the Qi 'an principal service team for many years in the service of various large government and enterprise organizations.
This book comprehensively explains the breakthrough of defense system from the perspective of blue team, the construction of defense system from the perspective of red team, and the actual attack and defense drill organization from the perspective of Purple team. It systematically introduces the process, method, means, ability and strategy that all parties should master in the Red and blue attack and defense actual drill, including comprehensive technical details and a large number of attack and defense practice cases.
The first part (Chapter 1) is the basis of Red versus Blue
First of all, this paper expounds the reasons for conducting actual combat offensive and defensive drills and the development status of actual combat offensive and defensive drills. Secondly, the definition and evolution trend of red team, basketball team and purple team are introduced. Finally, the weak links exposed in actual combat attack and defense drills and how to establish a real combat safety system are summarized.
Part Two (Chapter 2-5) Defense system breakthrough from the perspective of Blue Team
It explains the four stages of the blue team's defense breakthrough, eight attack means, various necessary abilities, and nearly 10 classic cases using different attack strategies.
The third part (Chapter 6~10) Defense system construction from the perspective of Red team
It explains the four implementation stages, eight defensive strategies, five types of defensive means and five types of key equipment of the Red team's defense system construction, as well as the classic defensive cases from major government and enterprise organizations.
The fourth part (Chapter 11~13) The actual combat offensive and defensive drill organization from the perspective of Purple Team
First of all, from the aspects of drill organizational elements, organizational form, organizational key and risk avoidance measures, this paper describes how to organize a real combat attack and defense drill as an organizer. Then, it introduces the work content of the organizer in detail from five stages: organizational planning, preliminary preparation, real combat attack and defense drill, emergency drill and drill summary. Finally, the overall planning and organization process of sand table exercise after the drill is finished are introduced.
About the author
Chian Principal Service team
Team is a team offensive and defensive technology as the core, under the big, the cloud data is focused on the threat detection and response, advisory planning, threat detection, offensive and defensive drills, sustained response, warning notices, safe operation and a series of actual combat service capabilities, can provide customers with the whole cycle security services professional network security and emergency response team.
The team is the leading security service team in China with a business scope covering the whole country. The service objects include network security regulators, leading enterprises and industry units in various industries and fields such as the Party and government, finance, operators, energy, central enterprises, media and civil aviation.
The team has a large number of experienced network security attack and defense experts, gathered domestic outstanding network security talents, created a number of important security cases in the forefront of the industry, and for many years in the actual combat attack and defense drill has achieved brilliant achievements in attack and defense, has become the leading team of attack and defense drill service.
The team has a Stargazing laboratory team that focuses on Internet application vulnerability mining and attack and defense research, and a Z-TEAM team that plays an important role in actual combat attack and defense drills and is good at organizing and implementing penetration attacks, providing strong technical support for network security services. Z-TEAM has developed several sets of practical technology warfare methods and supporting tools in the continuous exercise of real network confrontation. Especially in the aspects of Web attack and defense, social worker penetration, Intranet penetration and simulated APT attack, the team has solid technical strength and flexible technology warfare methods, and its actual combat ability is highly recognized by the industry.

-
Web security Attack and defense
(1篇评论)10.00 USDSuitable audience: This book is suitable for enterprise security personnel, research and development personnel, ordinary colleges and universities network security discipline teaching and reference books, and as a network security enthusiasts self-study book.
Web Security Zero Basics introduction
From penetration test information collection to penetration offense and defense, learning penetration test this book is enough
Security expert practical explanation, from the principle to the scenario application
Content abstract
This book from the simple to the deep, comprehensive, systematic introduction of the current popular high-risk vulnerability attack means and defense methods, and strive to make the language easy to understand, simple and clear examples, easy for readers to read and understand. Combined with specific cases to explain, readers can be immersive, quickly understand and master the mainstream vulnerability utilization technology and penetration testing skills. A background in penetration testing is not required for this book, but relevant experience will be helpful. This book can also be used as a teaching material for information security in universities and colleges.
Author's brief introduction
Xu Yan is a security researcher at the Yangtze River Delta Institute of Beijing Jiaotong University. I got involved in network security in 2002, and my main research direction is Intranet penetration and APT attack. I have rich experience in network security penetration. Has published a book "Network attack and defense practical research: Vulnerability exploitation and rights", has published a number of technical articles in "Hacker Defense", "Hacker X-Files", "Hacker Handbook", FreeBuf, 360 security customer, Ali Cloud Shield Prophet, Shouhao and other magazines and media. Li Wenxuan, common ID: Oblivion. He used to be a penetration test engineer of Tianrongxin, and now he is a security researcher of Qihoo 360 Attack and Defense Laboratory. He is good at penetration testing and radio security. He has been active in multiple vulnerability reporting platforms, reported multiple CVE vulnerabilities, and participated in the editorial review of 360 Security Quarterly. Dong-a Wang, common ID 0xExploit. He used to be the senior security consultant of Green Alliance Technology and Tianrongxin. Now he is the security director of Anhui Sanshi and the initiator of ATK team. Good at penetration testing and code audit, active in multiple vulnerability reporting platforms, reported thousands of security vulnerabilities, including multiple CNVD, CVE vulnerabilities. He has published several professional technical articles in FreeBuf, Green League Technology Quarterly and other magazines and media, and won many CTF competition rankings.
directory
Chapter 1 Information Collection for Penetration Testing 1
1.1 Collecting Domain Name Information 1
1.1.1 Whois Query 1
1.1.2 Record Information Query 2
1.2 Collecting Sensitive Information 2
1.3 Collecting Subdomain Name Information 4
1.4 Collecting Common Port Information 7
1.5 Fingerprint recognition 10
1.6 Searching for the Real IP Address 11
1.7 Collecting Sensitive Directory Files 14
1.8 Social Engineering 15
Chapter 2 Build vulnerability environment and actual combat 17
2.1 Installing LANMP 17 on a Linux VM
2.2 Installing WAMP 19 on a Windows VM
2.3 Build DVWA vulnerability environment 21
2.4 Building an SQL Injection Platform 23
2.5 Building XSS Test Platform 24
Chapter 3 Common penetration testing tools 28
3.1 SQLMap Details 28
3.1.1 Installing SQLMap 28
3.1.2 SQLMap Introduction 29
3.1.3 SQLMap Advanced: Parameter Description 36
3.1.4 SQLMap comes with an explanation to bypass script tamper 40
3.2 Details of Burp Suite 50
3.2.1 Installation of Burp Suite 50
3.2.2 Getting Started with Burp Suite 51
3.2.3 Burp Suite 55
3.3 Details of Nmap 70
3.3.1 Installing Nmap 71
3.3.2 Nmap 101
3.3.3 Nmap advanced 83
Chapter 4 Web Security Principles 90
4.1 Basics of SQL injection 90
4.1.1 Introduction to SQL injection 90
4.1.2 Principles of SQL injection 90
4.1.3 Knowledge Points related to MySQL injection 91
4.1.4 Union Injection Attack 95
4.1.5 Union Injection Code Analysis 99
4.1.6 Boolean Injection attack 99
4.1.7 Boolean Injection code analysis 103
4.1.8 Error injection attack 104
4.1.9 Error injection code analysis 106
4.2 SQL Injection advanced 107
4.2.1 Time Injection Attack 107
4.2.2 Time Injection code analysis 109
4.2.3 Stack Query Injection Attack 110
4.2.4 Stack Query Injection Code Analysis 112
4.2.5 Secondary Injection 113
4.2.6 Secondary Injection Code Analysis 114
4.2.7 Wide Byte Injection Attack 116
4.2.8 Wide Byte injection Code Analysis 119
4.2.9 cookie injection Attack 120
4.2.10 cookie Injection Code Analysis 121
4.2.11 base64 Injection Attack 122
4.2.12 base64 Injection Code Analysis 123
4.2.13 XFF Injection Attack 124
4.2.14 XFF Injection Code Analysis 125
4.3 SQL Injection Bypass Technology 126
4.3.1 Case bypass injection 126
4.3.2 Double write bypassing injection 128
4.3.3 Encoding bypasses injection 129
4.3.4 Inlining comments bypasses injection 131
4.3.5 SQL Injection Repair Suggestion 131
4.4 XSS base 135
4.4.1 XSS Vulnerabilities 135
4.4.2 XSS Vulnerability Principle 135
4.4.3 Reflective XSS Attack 137
4.4.4 Reflection XSS Code Analysis 138
4.4.5 Storage XSS Attack 139
4.4.6 Stored XSS code analysis 140
4.4.7 DOM XSS attack 142
4.4.8 DOM XSS Code analysis 143
4.5XSS advanced 144
4.5.1 XSS Common Statements and codes bypass 144
4.5.2 Testing XSS Vulnerability 145 using the XSS Platform
4.5.3 XSS Vulnerability Repair Suggestions 148
4.6 CSRF Vulnerability 148
4.6.1 Describes CSRF Vulnerability 148
4.6.2 Principle of CSRF Vulnerability 148
4.6.3 Using CSRF Vulnerability 149
4.6.4 Analyzing CSRF vulnerability code 151
4.6.5 CSRF Vulnerability Repair Suggestion 155
4.7 SSRF Vulnerability 155
4.7.1 This section describes SSRF Vulnerability 155
4.7.2 SSRF Vulnerability Principle 155
4.7.3 SSRF vulnerability utilization 156
4.7.4 SSRF Vulnerability Code Analysis 157
4.7.5 SSRF Vulnerability Repair Suggestions 157
4.8 Uploading a File 158
4.8.1 Describes the File Upload Vulnerability 158
4.8.2 Knowledge about File Uploading 158
4.8.3 JS Detecting Bypass Attack 158
4.8.4 JS Detection Bypass Attack Analysis 160
4.8.5 File Suffix Bypass Attack 161
4.8.6 File Suffixes Bypass Code Analysis 162
4.8.7 File Type Bypass Attack 163
4.8.8 File Type Bypassing Code Analysis 164
4.8.9 File Truncation Bypass Attack 166
4.8.10 File Truncation bypasses code analysis 167
4.8.11 Competition Condition Attack 169
4.8.12 Competitive Condition Code Analysis 169
4.8.13 File Upload Repair Suggestion 170
4.9 Brute Force Cracking 170
4.9.1 Describes Brute-force Cracking Vulnerability 170
4.9.2 Brute-force Vulnerability 171
4.9.3 Brute-force Cracking Vulnerability Code Analysis 172
4.9.4 Brute-force Cracking Suggestion 172
4.10 Run the 173 command
4.10.1 Introduction to Command Execution Vulnerability 173
4.10.2 Command Execution Vulnerability Attack 173
4.10.3 Command Execution Vulnerability Code Analysis 175
4.10.4 Executing Vulnerability Repair Suggestion 175
4.11 Logical Vulnerability Mining 175
4.11.1 Logical Vulnerability 175
4.11.2 Unauthorized Access Attack 176
4.11.3 Logic Vulnerability: Unauthorized access Code Analysis 177
4.11.4 Unauthorized Access Repair Suggestion 179
4.12 XXE Vulnerability 179
4.12.1 This section describes Vulnerability 179 of XXE
4.12.2 XXE vulnerability 180
4.12.3 XXE Vulnerability Code Analysis 180
4.12.4 XXE Vulnerability Repair Suggestion 181
4.13 Those things about WAF
4.13.1 This section describes WAF 181
4.13.2 WAF Judgment 182
4.13.3 Some WAF bypass methods 184
Chapter 5 Metasploit Technology 188
5.1 Introduction to Metasploit 188
5.2 Metasploit Foundation 190
5.2.1 Technical Terms 190
5.2.2 Infiltration Attack Step 191
5.3 Host Scan 191
5.3.1 Scanning for Ports Using an Auxiliary Module 191
5.3.2 Scanning for Services Using the Auxiliary Module 193
5.3.3 Scanning 193 using Nmap
5.4 Vulnerability Utilization 195
5.5 Post-Penetration Attack: Information Collection 199
5.5.1 Migrating a Process 200
5.5.2 System Command 201
5.5.3 File System Command 208
5.6 Post Penetration Attack: Permission increased by 210
5.6.1 Using WMIC actual combat MS16-032 Local overflow Vulnerability 211
5.6.2 Token Theft 216
5.6.3 Hash Attack 219
5.7 Post-Penetration attack: Porting vulnerability exploits code module 229
5.7.1 Vulnerability Introduction, principle and Countermeasures of MS17-010. 229
5.7.2 Porting and exploiting the MS17-010 vulnerability to exploit code 230
5.8 Rear Penetration attack: Backdoor 233
5.8.1 Operating System Backdoor 233
5.8.2 Web Backdoor 237
5.9 Intranet Attack Zone Penetration Test Example 242
5.9.1 This section describes the Osmotic environment 242
5.9.2 Upgrading Rights 242
5.9.3 Collecting Information 245
5.9.4 Obtaining Permission on a Server 247
5.9.5 PowerShell Finds the domain Management Online Server
5.9.6 Obtaining Domain Management Permissions 252
5.9.7 Logging In to Domain Control 254
5.9.8 SMB blasting Intranet 257
5.9.9 Clearing Logs 259
Chapter 6 PowerShell Attack Guide 261
6.1 PowerShell Technology 261
6.1.1 Introduction to PowerShell 261
6.1.2 Basic Concepts of PowerShell 263
6.1.3 PowerShell common command 264
6.2 PowerSploit 266
6.2.1 PowerSploit Installation 266
6.2.2 PowerSploit Script Attack Actual 268
6.2.3 PowerUp Attack Module Description 275
6.2.4 PowerUp Attack Module Actual Combat 284
6.3 Empire 291
6.3.1 Introduction to Empire 291
6.3.2 Installation of Empire 292
6.3.3 Setting Listener 293
6.3.4 Generating Trojan 296
6.3.5 Connecting Hosts and Basic Usage 306
6.3.6 Information Collection 310
6.3.7 Permission Promotion 319
6.3.8 Lateral Penetration 324
6.3.9 Rear Door 330
6.3.10 Empire rebounds to Metasploit 333
6.4 Nishang 334
6.4.1 Nishang 334
6.4.2 Nishang module attacks Actual Combat 338
6.4.3 PowerShell hides communication tunnel 343
6.4.4 WebShell Backdoor 347
6.4.5 Permission Promotion 348
Chapter 7 Case Analysis 364
7.1 Code Audit Instance Analysis 364
7.1.1 SQL Injection Vulnerability 364
7.1.2 File Deletion Vulnerability 366
7.1.3 File Upload Vulnerability 367
7.1.4 Adding Administrator Vulnerability 373
7.1.5 Competition Condition vulnerability 378
7.2 Analysis of penetration test examples 380
7.2.1 Background blasting 380
7.2.2 SSRF+Redis obtains WebShell 383
7.2.3 Side attack 388
7.2.4 Resetting Password 391
7.2.5 SQL Injection 393View All ↓
Preface/preface
The recommended sequence
After my old friend worked day and night, word by word, the book was finally published. I would like to express my thanks to the editor for bringing together many years of work experience into the book. I've been working in information security for 18 years, and I think this book is a great guide for anyone who wants to work in penetration testing. I in after reading the book, and friends say, I would recommend this book to Beijing zhong an nation institute of information technology "national 5 a-class information security personnel training" teaching material system and the "national information security emergency services personnel certification practice exam reference materials directory", an old friend replied, "the book of experiments will be launched soon, All the supporting experiments will be put on the cloud experimental platform of Honghei Network Security Academy for everyone to practice." It is a great blessing that readers will be able to read and practice at the same time!
I highly recommend professional penetration testing personnel, information security one
-
[Set of 5] Hacker attack and defense books
(1篇评论)50.00 USDContent abstract
In the Internet era, data security and personal privacy are challenged, and various novel attack technologies emerge in an endless stream. How can we better protect our data? White Hat on Web Security (Commemorative Edition) will take you into the world of Web security and introduce you to all aspects of Web security. Hackers are no longer mysterious, attack techniques are so old, small websites can find their own safe path. How do big companies do security, and why do they choose such a solution? You can find the answer in White Hats on Web Security (Commemorative Edition). Detailed analysis, so that you can not only "know", but also "know why".
"White hat on Web security (Commemorative edition)" according to the security treasure Vice president Wu Hanqing in the Internet company before several years of practical work experience and written, in the solution has a strong operability; In-depth analysis of many wrong methods and misunderstandings, security workers have a good reference value; The introduction of security development process and operation also has profound industry guidance significance. The content of the Commemorative Edition is the same as that of the previous edition. It is only a special edition published in multiple languages to commemorate the original work. Please select it as required.
Content abstract
This book summarizes the causes, attack methods and solutions of the current popular high-risk vulnerabilities, and reproduces the vulnerability prototype through a large number of sample code, making a simulation environment, to better help readers to understand the vulnerabilities in Web applications, and prevent them from happening.
This book introduces the Web security system step by step, from attack to defense, from principle to actual combat. The book is divided into 4 chapters and 16 chapters. In addition to introducing the basic knowledge of Web security, it also introduces the common security vulnerabilities in Web applications, the attack flow and defense of open source programs, and focuses on analyzing the attack means used by hackers in the event of "drag library". In addition, some other detection methods of penetration test engineers are also introduced.
Content abstract
This book is a comprehensive and systematic introduction to the means of Intranet attack and defense, and strives to make the language easy to understand, simple and clear examples, easy to read and understand. At the same time, combined with specific cases to explain, readers can be immersive, quickly understand and master the mainstream Intranet vulnerability utilization technology and Intranet penetration testing skills.
A background in penetration testing is not required; It will be easier to understand if you have relevant experience. This book can also be used as a teaching material for information security in universities and colleges.
-
Linux Programming
(1篇评论)8.00 USDThis book describes the development of programs on Linux and other UNIX-style operating systems, mainly including the standard Linux C language library and the use of various tools by different Linux or UNIX standards, the use of most of the standard Linux development tools, Through DBM and MySQL data store Linux data, for X window system to establish a graphical user interface. This book helps the reader grasp the relevant knowledge by first introducing the theory of programming and then clarifying it with appropriate examples and clear explanations. This book is suitable for beginners of Linux and those who want to use Linu line development programs, and it is also suitable as a reference for teachers and students of computer related majors in universities.
Chapter 1 Introduction
1.1 Introduction to LNIX, Linux, and GNU
1.1.1 What is IYNIX
1.1.2 What Is Linux
1.1.3 GNL, projects and free software will
1.1.4 Linux distribution
1.2 Linux programming.
1.2.1 Linux program
1.2.2 Text Editor
1.2.3 C language compiler
1.2.4 Development system guidance
1.3 Getting Help
1.4 summary
Chapter 2 shell programming
2.1 Why Use shell Programming
2.2 A little Philosophy
2.3 What is shell
2.4 Pipes and redirection
2.4.1 Redirecting output
2.4.2 Redirection Input
2.4.3 pipeline
2.5 shell as a programming language
2.5.1 Interactive program
2.5.2 Creating a Script
2.5.3 Making the Script Executable
2.6 shell syntax
2.6.1 variable
2.6.2 conditions
2.6.3 Control structure
2.6.4 function
2.6.5 command
2.6.6 Executing Commands
2.6.7 aere 1 document
2.6.8 Debugging the script
2.7 Towards Graphics: dialog tool
2.8 Comprehensive Application
2.8.1 demand
2.8.2 design
2.8.3 Description of Applications
2.9 summary
Chapter 3 File operations.
3.1 Linux file structure
3.1.1 directory
3.1.2 Files and Devices
3.2 System calls and device drivers
3.3 library function
3.4 Accessing Underlying Files
3.4.1 write the system Call
3.4.2 read the system Call
3.4.3 open System call -
Kali Linux Wireless penetration
(1篇评论)6.00 USDWireless network is ubiquitous in our life and wireless penetration testing has become an important skill for security practitioners. And with the advent of a KRACK attack, which can be used by an attacker to breach a WiFi network that uses WPA2 encryption, wireless penetration testing is once again in the spotlight. Kali Linux comes with a number of tools for detecting security vulnerabilities and can be used to perform a variety of network testing tasks.
The book provides a comprehensive update to the emerging methodologies, covering the principles of a KRACK attack and the methods to defend against it. This book explains the knowledge of wireless penetration testing from the ground up, introduces all the relevant content of each penetration testing technology, and demonstrates the methodology of wireless testing with a large number of cases. The reader will learn the basics of wireless routing and encryption, as well as the details of various cracking methods and attacks such as Hirte and Caffe Latted.Contents of the Book:
Fully understand the KRACK attack;
Create a wireless test environment;
Sniffing wireless packets, hidden networks and SSIDs;
Capture and crack WPA2 keys;
Sniff probe requests and track users through their SSID history;
The RADIUS authentication system is attacked.
Sniff wireless traffic to collect data of interest;
Decrypt encrypted traffic using stolen keys.Content abstract
This introductory guide to penetration testing in the wireless space is fully updated for Kali Linux 2017.3 and aims to help readers understand the various security vulnerabilities associated with wireless networks and how penetration testing can be used to find and plug them.
The book is divided into 11 chapters, including how to build a wireless network testing environment using off-the-shelf hardware and open source software, WLAN and its inherent security risks, ways to circumvent WLAN verification, understanding the drawbacks of WLAN encryption, how to take advantage of these drawbacks to solve WLAN encryption, how to conduct penetration testing of WLAN infrastructure, and how to use WLAN encryption to test WLAN infrastructure. And how to launch various wireless client attacks to compromise network security. In addition, it covers today's cutting-edge wireless attack methods, new methods of KRACK attack, attacking WPA-Enterprise and RADIUS, the principles of WLAN penetration testing, and WPS brute force attacks and detection-sniffing attacks.
This book is for readers who are interested in wireless penetration testing and have a basic knowledge of wireless networks.Author's brief introduction
Cameron Buchanan is a penetration testing practitioner and amateur writer who has done penetration testing work for many clients in various industries around the world. Cameron previously served in the Royal Air Force (RAF). In his spare time, he likes to do "stupid things", such as trying to make something fly, getting electrocuted, and taking a dip in ice water. He is married and lives in London.
Vivek Ramachandran has been working on WiFi security since 2003. He discovered the Caffe Latte attack, cracked the WEP Cloaking (a WEP protection scheme), and publicly released it at DEF CON in 2007. In 2011, he demonstrated how malware could be used to create backdoors, worms and even botnets through WiFi.
Previously, Vivek worked for Cisco as a programmer of 802.1x protocol and port Security features for the 6500 Catalyst series switches, and was one of the winners of the Microsoft Security Shootout in India. He is well known in the hacker community and posts videos about WiFi security, assembly language, and hacking techniques.
Vivek's achievements in wireless security have been covered by several media outlets (BBC Online, InfoWorld, MacWorld, The Register and IT World Canada, among others). This year, he will be speaking and training at several security conferences (Blackhat, DEF CON, Hacktivity, 44con, HITB-ML, BruCON Derbycon, Hashdays, SecurityZone and SecurityByte, among others).directory
Chapter 1 Build wireless experimental environment 1
1.1 Hardware Requirements 2
1.2 Software Requirements 2
1.3 Installing Kali 3
1.4 Hands-on experiment - Install Kali 3
Experiment Description 5
Try to break through - install Kali 5 in VirtualBox
1.5 Configuring AP 5
1.6 Hands-on experiment - Configure wireless AP 6
Experiment Description 8
Try to break through - Configure AP, enable WEP and WPA 8
1.7 Configuring a Wireless NIC 8
1.8 Hands-on Experiment - Configuring a wireless NIC 8
Experiment Description 9
1.9 Connecting to AP 9
1.10 Hands-on Experiment - Configure a wireless NIC 10
Experiment Description 12
Try to break through - Establish a wireless network connection in WEP mode 12
Pop Quiz - Mastering the Basics 12
1.11 Summary 13Chapter 2 WLAN and Its Inherent Pitfalls 14
2.1 Revisiting WLAN Frame 15
2.2 Hands-on Experiment - Create an interface running in monitoring mode 17
Experiment Description 20
Try to break out - Create multiple interfaces in monitor mode 20
2.3 Hands-on experiment -- Capture wireless packet 20
Experiment Description 22
Try to break through - Discover other devices 22
2.4 Hands-on experiment -- Viewing management, control and data frame 23
Experiment Description 25
Try breaking out - Play with Wireshark Filters 26
2.5 Hands-on Experiment - Data Packet Theft in Experimental Environment 27
Experiment Description 28
Try to break through - Analyze packet 29
2.6 Hands-on Experiment - Packet Injection 29
Experiment Description 30
Try breaking through -- aireplay-ng tool with other options 30
2.7 Important Matters related to WLAN packet capture and injection
2.8 Hands-on experiment - Set a wireless NIC 31
Experiment Description 32
Attempt to break through - Multi-channel Packet Capture 32
In-class quiz - WLAN packet capture and injection 32
2.9 Summary 33Chapter 3 Circumventing WLAN authentication 35
3.1 Hidden SSID 35
3.2 Hands-on experiment -- Discover hidden SSID 36
Experimental Description 41
Try to break through -- Targeted de-validation 41
3.3 MAC Filter 41
3.4 Hands-on Experiment - Defeat MAC filter 42
Experimental Description 44
3.5 Open Validation 45
3.6 Hands-on Experiments -- Bypassing open validation 45
Experimental Description 46
3.7 Shared Key Verification (SKA) 46
3.8 Hands-on Experiments -- Bypassing shared validation 47
Experimental Description 52
Common sense breakthrough - Fill the wireless client table 52 saved by the AP
In-class quiz -- WLAN Verification 52
3.9 Summary 53Chapter 4 WLAN Encryption Vulnerabilities 54
4.1 WLAN Encryption 54
4.2 WEP encryption 55
4.3 Hands-on experiment -- Crack WEP 55
Experimental Instructions 62
Attempt to break through - Spoofing verification with WEP cracking attacks 63
4.4 WPA WPA2 63
4.5 Hands-on Experiment - Crack WPA-PSK weak password 66
Experimental Description 70
Try to break through - Try to crack WPA-PSK 71 with Cowpatty
4.6 Cracking WPA WPA2 PSK 71
4.7 Hands-on experiment -- Speed up the cracking progress
Description of Experiment 73
4.8 Decrypt WEP and WPA packets 73
4.9 Hands-on experiment - Decrypt WEP and WPA packet 74
Experiment Description 75
4.10 Connecting to WEP and WPA networks 75
4.11 Hands-on Experiment -- Connect to WEP network 76
Experimental Description 76
4.12 Hands-on Experiment -- Connect to WPA network 76
Description of Experiment 77
In-class quiz -- WLAN Encryption Vulnerability 77
4.13 Summary 78Chapter 5 Attacking the WLAN Infrastructure 79
5.1 Exploit the holes in the default AP account and default "Pass" 79
5.2 Hands-on Experiment - Crack the default AP account 80
Experimental Description 80
Try to break through - break into an account by brute force 81
5.3 Denial of Service Attack 81
5.4 Hands-on Experiment - Disverify the DoS attack 81
Description of Experiment 84
Try to break through 84
5.5 evil twin and AP MAC Address Spoofing Attacks 85
5.6 Hands-on Experiment - evil twin Attack with MAC Address Spoofing 85
Experimental Description 88
Try to Break out -- evil twin and channel hopping Attack 89
5.7 Rogue AP 89
5.8 Hands-on experiment - Set up rogue AP 89
Experimental Description 92
Try to break through - the building of the difficult Rogue AP 92
In-class Quiz -- Attacking the WLAN Infrastructure 92
5.9 Summary 93Chapter 6 Attacking Wireless Clients 94
6.1 Honeypot and misassociation Attack 95
6.2 Hands-on Experiment - Launch false association Attack 95
Experiment Description 100
Try to break through - force wireless clients to connect to Honeypot 100
6.3 Caffe Latte attacks 100
6.4 Hands-on Experiment - Launch Caffe Latte Attack 101
Experimental Description 103
Common sense breakthrough - practice makes real knowledge! 103
6.5 Disverifying and Disassociating Attacks 104
6.6 Hands-on Experiment - Unauthenticate the wireless client 104
Experimental Description 107
Attempt Breakthrough - Cancel association attack against wireless clients 107
6.7 Hirte Attack 107
6.8 Hands-on Experiment -- Launch WEP Hack Hirte Attack 108
Experimental Description 109
Try to break through - Practice, Practice, Practice 110
6.9 Crack WPA-Personal 110 without touching the AP
6.10 Hands-on Experiment - Crack WPA 111 without touching AP
Experimental Instructions 113
Attempt a breakthrough - Crack WPA 113 without touching the AP
Quiz in class - Attacking Wireless client 113
6.11 Summary 114Chapter 7 Advanced WLAN Attacks 115
7.1 Man-in-the-Middle Attack 115
7.2 Hands-on Experiment -- Man-in-the-Middle Attack 116
Experimental Description 120
Attempt to break through - Launch MITM attack over pure wireless network 120
7.3 Wireless Network Eavesdropping based on MITM 121
7.4 Hands-on Experiment - Wireless Network Eavesdropping 121
Experiment Description 123
7.5 Session Hijacking Attacks on Wireless Networks 123
7.6 Hands-on Experiment - Session Hijacking in Wireless Network 124
Experimental Description 127
Attempt to Break through - High difficulty application hijack 128
7.7 Understanding the security configuration of a wireless client for a wireless network 128
7.8 Hands-on Experiment - Launch the De-validation attack 129 for wireless clients
Experiment Description 132
Try to break 132
In-class Quiz - Advanced WLAN Attack 132
7.9 Summary 133Chapter 8 KRACK Attack 134
8.1 Overview of KRACK Attacks 134
Experimental Description 136
8.2 Four Handshake KRACK Attack 136
8.3 Hands-on Experiment - Launch KRACK 137
Experimental Description 141
8.4 Summary 142Chapter 9 Attacks WPA-Enterprise and RADIUS 143
9.1 Installing FreeRADIUS-WPE 143
9.2 Hands-on experiment -- Setting up AP and FreeRADIUS-WPE 144
Experimental Description 147
Try to break through - Play RADIUS 147
9.3 Attacking PEAP 148
9.4 Hands-on Experiment - Crack PEAP 148
Experimental Description 151
Attempt to break through - Mutant attack 151 against PEAP
9.5 EAP-TTLS 151
9.6 WPA-Enterprise Security Best Practices 152
Quiz in class - Attack WPA-Enterprise and RADIUS 152
9.7 Summary 153Chapter 10 WLAN Penetration Testing 154
10.1 Wireless Penetration Test 154
10.2 Planning Phase 155
10.3 Discovery Phase 156
10.4 Attack Phase 156
10.4.1 Cracking Encryption 157
10.4.2 Attacking Wireless Network Infrastructure 158
10.4.3 Attacking a Wireless Client 158
10.5 Report phase 158
10.6 Summary 159Chapter 11 WPS and Detection 160
11.1 WPS Attack 160
11.2 Hands-on Experiment - WPS Attack 161
Description of Experiment 164
Attempt to breach - Rate limit 165
11.3 Probe sniffing 165
11.4 Hands-on Experiment - Data Collection 166
Experimental Description 170
Try to break through -- Open your mind
11.5 Summary 171
Pop quiz answer 172 -
Hacker attack and defense from entry to mastery
(1篇评论)10.00 USD"Hacker Attack and Defense from entry to mastery (Encryption and Decryption)" covers from the introduction of computer hacking attack and defense, to professional Web technology security knowledge, suitable for all levels of readers with different foundations.
Hacking from Beginner to Proficient (Encryption and Decryption) is intended for users of Windows 7 and later operating systems. Although many of the tools and cases in this book can be run or used under Windows XP and other systems, it is strongly recommended that readers install Windows 7 or later in order to learn the full content of this book.
Hacker Attack and Defense from Entry to Mastery (Encryption and Decryption) is a combination of theories and examples. After the introduction of relevant knowledge points, the knowledge points are introduced in the form of cases, so as to deepen readers' understanding and cognitive ability of the knowledge points and strive to comprehensively master the knowledge points.
"Hacker Attack and Defense from Entry to Master (Encryption and Decryption)" abandoned a large number of dry text narrative writing, but adopted a graphic way to layout, with a large number of illustrations to explain, can make the learning process easier for readers.
The content of Hacker Attack and Defense from Entry to Mastery (Encryption and Decryption) starts from zero, is easy to understand, and is explained from simple to deep, so that both beginners and users with a certain base can gradually improve.
Content abstract
"Hacker Attack and defense from entry to master (encryption and Decryption section)" from the simple to the deep, illustrated and reproduced the computer and mobile phone security related knowledge. The book consists of 22 chapters, including social engineering, Computer and Network Anti-hacking Basics, Windows 10 Firewall and Windows Defender, Windows 10 Advanced Security Management, system and data backup and recovery, computer and network control commands, scanning and sniffing: Determine the target and explore network resources, Trojan horse prevention technology, virus prevention technology, Windows system vulnerability attack and defense technology, computer backdoor technology, program encryption and decryption technology, LAN security prevention Technology, computer remote control technology, Web site security prevention technology, cleaning malicious plug-ins and software, online games and Internet cafe security prevention technology, online account anti-hacking combat, online payment tools.
Author's brief introduction
Libo Zong has been working at Inspur Group since 2010 and is currently the information security Manager. Over the years, he has participated in editing and editing many books on computer and network security.
Inside pages illustrations
directory
directory
Chapter 1 Social Engineering
1.1 Hacking and Social Engineering
1.1.1 Overview of Social engineering attacks
1.1.2 Non-traditional information security that cannot be ignored
1.1.3 Attack Information Owner
1.2 Uncovering common social engineering attacks
1.3 Social engineering attacks happen all the time
1.3.1 Obtaining a User's Mobile Phone Number Illegally
1.3.2 Uncovering phishing
1.3.3 How Do I Fake my Identity to obtain system Passwords
1.4 Ubiquitous information search....

![White Hat on Web Security [Commemorative Edition]](https://www.hackhat.org/uploads/monthly_2022_11/1149273819_.png.d79b69517b4f68a233e8eef183b62be7.png)







![[Set of 5] Hacker attack and defense books](https://www.hackhat.org/uploads/monthly_2022_11/1840350085__FRJO)UE22DD5B8CWW.png.bff4a416f7cae963e50ffaa7251d7b89.png)


.thumb.jpg.1de85edaa56ac15b1096a291232e91d6.jpg)
18KAH1O3OV9ZKJCM.png.2139f875c42cd1a18a840e754547fa8d.png)
3BQRW2GH_9H.png.c32c2daa8be815526ae646c9dee56213.png)



PK.png.a9bf011e416a6dc91dccb6b56d40d95e.png)